Network Security
Learn about Verrazzano network security
A Verrazzano instance is comprised of both Verrazzano components and several third party products. Collectively, these components are called the Verrazzano system components. In addition, after Verrazzano is installed, a Verrazzano instance can include applications deployed by the user. Applications can also be referred to as components, not to be confused with OAM Components.
All of the system components and applications use the network to some degree. Verrazzano configures networking to provide network security and traffic management. Network settings are configured both at installation and during runtime as applications are deployed into the Kubernetes cluster.
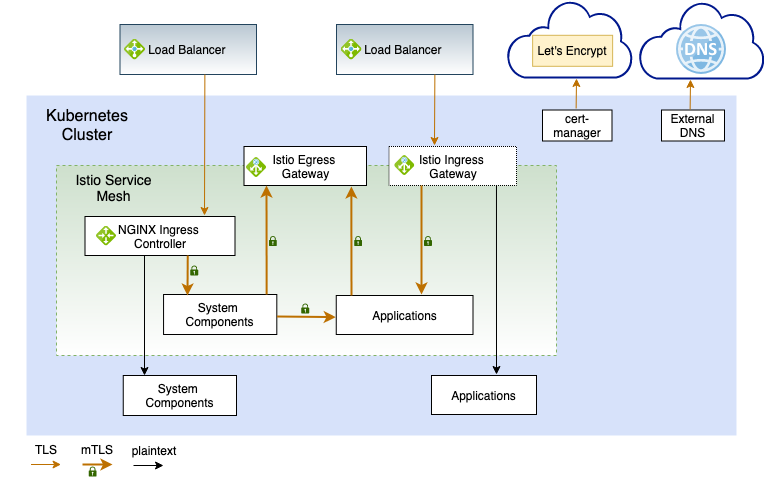
The following diagram shows the high-level overview of Verrazzano networking using ExternalDNS and Let’s Encrypt for certificates. ExternalDNS and cert-manager both run outside the mesh and connect to external services using TLS. This diagram does not show Prometheus scraping.
Verrazzano system traffic enters a platform load balancer over TLS and is routed to the NGINX Ingress Controller, where TLS is terminated. From there, the traffic is routed to one of the system components in the mesh over mutual TLS authentication (mTLS), or using HTTP to a system component, outside the mesh.
Application traffic enters a second Oracle Cloud Infrastructure load balancer over TLS and is routed to the Istio ingress gateway, where TLS is terminated. From there, the traffic is routed to one of several applications using mTLS.
NOTE: Applications can be deployed outside the mesh, but the Istio ingress gateway will send traffic to them using plain text. You need to do some additional configuration to enable TLS passthrough, as described at Istio Gateway Passthrough.
A Kubernetes cluster is installed on a platform, such as Oracle OKE, an on-premises installation, a hybrid cloud topology, or such. Verrazzano interfaces only with Kubernetes; it has no knowledge of platform topology or network security. You must ensure that there is network connectivity. For example, the ingresses might use a platform load balancer that provides the entry point into the cluster for Verrazzano consoles and applications. These load balancer IP addresses must be accessible for your users. In the multicluster case, clusters might be on different platform technologies with firewalls between them. Again, you must ensure that the clusters have network connectivity.
A summary of the network-related configuration follows.
Verrazzano does the following as it relates to networking:
Verrazzano does the following as it relates to applications being deployed and terminated:
Learn about Verrazzano network security
Understand Verrazzano network traffic
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.